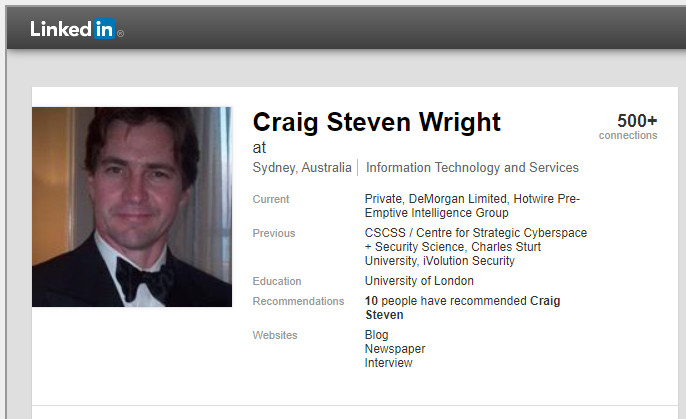
Craig Steven Wright. perfil de Linkedin antiguo
Craig Steven Wright
at
- Sydney, Australia
- Information Technology and Services
| Current |
|
|---|---|
| Previous |
|
| Education |
|
| Recommendations | 10 people have recommended Craig Steven |
| Websites |
Summary
SENIOR MANAGEMENT EXECUTIVE INFORMATION SECURITY SPECIALIST
► CTO / CIO / CISO /CSO
Multi-certified Expert in Enterprise Security and Cloud Strategies
If you want to sell me SEO, look at what I do first.
http://www.top500.org/site/50547
Respected executive and technology leader delivering proven ability to capitalize on enterprise-level technologies and pioneering strategies. A sought-after internationally recognized author and public speaker, delivering solutions to government and corporate departments in SCADA security, Cyber Security and Cyber Defense, as well as leading the uptake of IPv6 and Cloud technologies. Drives innovative strategies that result in the strategic redevelopment and invigoration of both startups and established firms. Futurist, thought leader and expert with proven innovation in program leadership, execution design and strategic redevelopment.
► Technology Leadership Results
Trusted member of senior executive team driving results driven innovation focused strategies that take core business competencies and deliver profitable client centric results and growth.
► Centre of Excellence Leader delivering to government and corporate clients pathways to IPv6 and secure cloud based solutions.
► Led the migration of a new core banking platform based on .Net and cloud technologies delivering a forward client centered banking platform.
► Oversight and governance in the profitable management of a $5 billion financial trust.
Distinguished by designing the security architecture and environment for Lasseter’s On-Line Casino allowing approval by the NT Government for the first online gaming license globally.
Developed board level security policies and procedural practices within Mahindra and Mahindra, India’s largest vehicle manufacturer. The Mahindra group employee over 50,000 people in total and has numerous business interests from Car to Tractor manufacture, through to IT outsourcing.
Experience
-
Chief Scientist
Private
– Present (6 months)Writing papers,
Research,
Managing change.Nothing but security and blockchain
-
Chief Executive Officer
DeMorgan Limited
– Present (1 year 4 months)DeMorgan is a pre-IPO Australian listed company focused on alternative currency, next generation banking and reputational and educational products with a focus on security and creating a simple user experience.
We control the following companies:
• Panopticrypt Pty Ltd
• Cloudcroft Pty Ltd
• Coin-Exch Pty Ltd
• C01N Pty Ltd
• CHAOS AND NONLINEAR FORECASTABILITY IN ECONOMICS AND FINANCE PTY. LTD.
• DASO Pty Ltd
• Denariuz Pty Ltd
• Denariuz Pte Ltd (Singapore)
• EzAs Pty Ltd
• Integyrz Pty Ltd
• DeMorgan Ltd (Panama)
• Pholus Pty Ltd
• Zuhl Pty Ltd
• Zuhl Corp Ltd (USA)
• Misfit Games Pty Ltd
• Denariuz Ltd (UK)Our group of companies has received a series of Advance Findings from AusIndustry around the two HPC systems we run and the AI and machine learning activities we conduct. In total, we have received Core Technology and Advance Finding certificates for 110 million in research activities.
In the six years since the first company in the group started, we have completed several Bitcoin based research projects that have lasted over and are now ready to start commercialising.
-
Chief Executive Officer
Hotwire Pre-Emptive Intelligence Group
– Present (2 years 7 months)Sydney, AustraliaResponsible for direction and business development as well as development of programs and services.
We are a group of highly technical individuals that make up a growing team. This position is based in our Sydney office, with travel to Brisbane and California.
The world grows through change and knowledge. To thrive, people need to develop wisdom in a social web. To enable this, we must look ahead, understand the trends and forces that will shape society and business in the future and move swiftly to prepare people for what’s to come. We will help the world to get ready for tomorrow today. That’s what our 2020 Vision is all about. It creates a long-term destination for our business and provides us with a «Roadmap» for winning together with our community and the society we will help to foster through trust and assurance.
Our Mission
Our Roadmap starts with our mission, which is enduring. It declares our purpose as a company and serves as the standard against which we weigh our actions and decisions.
• To make the world wiser and better…
• To inspire enduring optimism and trust…
• To create value and make a difference.Hotwiring the world
The world grows through change and knowledge. To thrive, people need to develop wisdom in a social web. To enable this, Hotwire PE must look ahead, understand the trends and forces that will shape society and business in the future and move swiftly to prepare people for what’s to come. We will help the world to get ready for tomorrow today. That’s what our 2020 Vision is all about. It creates a long-term destination for our business and provides us with a «Roadmap» for winning together with our community and the society we will help to foster through trust and assurance. -
Trustee
The Uniting Church (NSW) Trust Association Limited
– Present (8 years 1 month)United Financial Services Trustee
Financial services are provided by The Uniting Church (NSW) Trust Association Limited ACN 000 022 480, ABN 89 725 654 978, AFSL 292186 and by The Uniting Church in Australia Property Trust (NSW) -
Author and Technical Editor
Various Publishers
– Present (16 years 1 month)I am working on the legal section of the CISSP/ISSMP handbook for ISC2 and a book on MMC (Syngress) – Mobile Malicious Code. At the moment.
My latest book to be released is:
«The IT Regulatory and Standards Compliance Handbook:
How to Survive Information Systems Audit and Assessments»Publisher: Syngress (June 21, 2008)
Language: English
ISBN-10: 1597492663
ISBN-13: 978-1597492669
http://www.amazon.com/Regulatory-Standards-Compliance-Handbook-Information/dp/1597492663 -
Executive Vice President, Strategic Development
CSCSS / Centre for Strategic Cyberspace + Security Science
– (3 years 7 months)London, United KingdomResponsible for direction and business development within the Asia Pacific region as well as development of programs and services.
The Centre for Strategic Cyberspace + Security Science (CSCSS) is a multilateral, international not-for-profit organization that conducts independent cyber-centric research, development, analysis, and training in the areas of cyberspace, defence intelligence, cyber security, and science while addressing the threats, trends, and opportunities shaping international security policies and national cyberspace cyber security initiatives.
CSCSS, as a strategic leader in cyberspace, works jointly with key partners to address, develop, and define cyber technologies, cyber defence force capabilities, information dominance, and concept operations. We deliver practical recommendations and innovative solutions and strategies to advance a secure cyberspace domain.
CSCSS focuses on research and development in cyberspace, cyber-science, and cyber-security to find strategic insights and solutions. Our areas of operations are:
•The Cyberspace Group
•The Cyber Warfare Centre (CWC)
•The Cyberspace Science Research + Development (CSRD) Group
•The Cyberspace Modelling + Simulation Centre (CMSC)
•The Critical Infrastructure Protection (CIP) Group
•The Enterprise Technology + Security Consortium
•Cyber Security Training (Classified/Unclassified)
These groups focus on issues related to:•Defence and Cyber Security
•Information Defence/Information Dominance
•Cyber Training, Education, and Science
•Cyber Crime/eCrime
•Cyberspace Science Operation
•Global Response for Cyberspace
•Cyber Incident Response
•International Cyberspace Relations
•Joint Cyber Unit (JCU) hosted by CSCSS
•Cyberspace Network Integration
•Public-Private Sector Collaboration on Cyberspace and Security
•Cyber Emergency Readiness
•Creation of National Cyber Security Programs
•Minerva Projects -
Subject Coordinator/Lecturer
Charles Sturt University
– (5 years 6 months)Developed and promoted the Masters degree in Digital Forensics at CSU.
I am the subject coordinator for several subjects including –
– ITE 50x Mobile Coding (Windows)
– ITE 504 Windows Communication Foundation (Visual Studio 2010, C#)
– ITE 512 Incident Handling
– ITE 513 Digital Forensic Investigation
– ITE 514 Professional Systems Security (CISSP)
– ITE 516 Penetration Testing
– ITE 525 Cyberlaw
– ITE 539 Mail Server Implementation & Administration
– ITI 535 Networking and Operating System Essentials
– MGT 513 Enterprise Project ManagementI promote the IT Masters degree in digital forensics that I helped to create.This is a industry aligned coursework masters degree.
On top of this I am in the final stages of completing and having a subject approved in Windows Mobile and Cloud Coding. This is an innovative course in programming for the Windows Tablet and Phone marketplace using cloud based technologies.
I offer the following cloud based and crowd sourced courses:
– Statistics
– Cyber Crime
– Reverse Engineering Software -
Vice President, Forensics Services
iVolution Security
– (6 years 2 months)As Vice President, Forensics Services, Dr. Craig Wright is responsible for setting iVOLUTION Security’s strategic direction in the forensics field and is responsible for overseeing the development, testing and deployment of all forensics services and products.
-
Technical Director
GIAC
– (8 years)I am a SANS Technical Director
I am on the GIAC Ethics Board until standing down and leaving room for new blood (2011) -
Mentor and Stay Sharp Instructor
SANS Institute
– (8 years)Various security courses:
http://www.sans.org/instructors/craig-wrightI have taught:
SEC 504 http://www.sans.org/course/hacker-techniques-exploits-incident-handlingSEC 560 http://www.sans.org/course/network-penetration-testing-ethical-hacking
SEC 660 http://www.sans.org/course/advanced-penetration-testing-exploits-ethical-hacking
SEC 508 http://www.sans.org/course/advanced-computer-forensic-analysis-incident-response
SEC 401 http://www.sans.org/course/security-essentials-bootcamp-style
LEG 523 http://www.sans.org/course/law-data-security-investigations
AUD 507 http://www.sans.org/course/auditing-networks-perimeters-systems
-
VP, Asia Pac
Whitehats Conference
– (4 years 7 months)Whitehats Conference brings together innovative, ground-breaking information security technologies, and also provides access to leaders, experts, and luminaries in the IT security field. Whitehats Conference delivers knowledge, critical insight, and awareness into current and emerging whitehat technologies, organizations, and trends, and explores their potential impact on business environments.
-
Asia Pacific Director, VP
GICSR | Global Institute for Cyber Security + Research
– (11 months)Delivery of vision in Strengthening cyberspace at an organizational, national, and international level, protecting key elements of the information and critical infrastructure which are crucial to the continued delivery of essential services and national security.
Responsible for strategic direction and business development within the Asia Pacific region. Establishment of executive level relationships with the National Security Agency (NSA), Department of Homeland Security (DHS), North American Space Administration and DSD and regional government bodies. Formation of a multinational cconsortium providing information systems assurance and information security engineering and architecture services to promote the secure design and development of information services, technologies, communications, products, and systems. We deliver tactical IA solutions and frameworks. Executive management of the CSRD Group leveraging strategic partnerships with the public-private sector, academia, and international agencies to enable an innovative-collaborative approach to R&D.
-
CEO
GreyFog
– (2 years 3 months)Greyfog developed security software and solutions to the digital media industry. We worked with Watt Watchers and developed a small footprint security device for the transmission of digital media.
This company was sold for the licensing rights of the business after the successful deployment of a national VPN and firewall infrastructure managing an international cinema chain was deployed.
-
Chief Software Officer, Director
Integyrs Pty Ltd
– (2 years 4 months)Algorithmic and Secure Software design and code analysis.
Leading a software team in modeling of risk using hazard survival models. Creating a package of .Net libraries for audit clients, Digital Forensics and design of statistical tests for accounting and financial systems.
Responsible lead on a packer analysis project designed to improve the efficiency of malware detection in the CA Vet Anti-Virus platform. Creation of DATs (Digital Analysis Technology) for a Marine Sales Company in NSW. Static Code analysis for a major multinational gaming company.
-
Director
Information Defense Pty Ltd
– (2 years 6 months)Information defense was sold to Cloudcroft in 2011.
Key achievements in this role:
– Project management and operational deployment of a nationwide (Australia and NZ) deployment of a managed IDS, Firewall, SIEM and logging platform for an advanced media company across 45 geographically segmented locations each requiring a meshed series of network security devices.– Core Banking review and implementation for a major credit union.
– Code security maintenance and project management on Database (SQL, SAS) and Web projects for a major online sport’s betting and casino operation.
Digital Forensics, Information and Data Protection Services.
Information Defense provides the knowledge and skills to ensure that your data remains safe, secure and accurate. Like most companies of our class, we provide services to defend against cyber crime and online fraud. Unlike most (if not all) we also have the skills to ensure that your data is accurate. Combining the highest level of digital forensic, information security and statistical skills in a single entity allows us to offer you the solution that you need to ensure that your data is safe.
-
Associate Director (Risk Services)
BDO
– (4 years 4 months)Security risk assessments, (Based on HIPPA, AS/NZS 4360 and various sections of the financial services legislation),
Project managed the implementation of a secure remote access and token authentication system.
Implemented and lead a project to design and deploy ISO 17799 aligned policy and procedures within numerous companies both in Australia and Internationally through a consultative process.
Developed ISO17799 and AS/NZS 4360 audit and review frameworks
Has produced academically published papers on IT, Mathematics, HR and Business Strategy
I Manage the following Business lines:
Data Analysis Team
Data Mining Team
IT Forensic Team
IT Audit Team
IT Security TeamI specialise in:
• Associative Rules Mining
• Memory Forensics
• Embedded device Forensics
• Network Forensics
• Cryptanalysis
• System incident recovery (“deep diving”)
• Steganography -
Chief Research Officer (1-100 Employees, R and D Company)
Ridges Estate
– (3 years 8 months)Implemented an AusIndustry approved Research Program involving the integration of technical solutions to the information security and agribusiness arenas.
Creation of Firewall and Authentication Procedure documents for News Ltd
Mentoring at News Ltd in Security Technologies
Risk Assessments for News Ltd based on AS4360
Audit activity for News Ltd of the Internet systems and Firewalls
Staff training of the SecurID Authorisation systems
Network Security audit of the RIC Systems Internet Gateways
DNS and Mail Systems Security for RICVirus containment activities for RIC
Policy creation for Vodafone Ltd
Risk Assessments for Vodafone
Training and documentation of Security Audit and review procedures for Vodafone
Wireless researchCraig lead a research team that conducted technology research into –
Wireless systems research
IT Security Systems
Encryption Techniology
Agricultural Automation and monitoring systems
Farm Management Software
Malware Systems -
Managing Director
DeMorgan
– (5 years 10 months)MD, CTO, CIO and founder.
Founded one of the first providers of IT security services specializing in managed security and secure systems design to the top 150 companies in Australia with a focus on the financial services, banking and technology markets.
Executive management of IT consultants, administrative and helpdesk staff with between 20-26 direct reports in 15 global locations.
-
Information Security
Australian Stock Exchange
– (1 year 2 months)Security, Firewalls and IDS.
-
Corporate Accounts Manager
OzEmail
– (1 year)Managing a bunch of engineers in the pre-dot.com bubble days
-
Network Manager
Corporate Express (WPA)
– (4 years)General gopher and person people blamed when computers failed
-
All sorts
WPA
– (3 years)Fixing stuff
-
Executive Chef
C&C Catering
– (3 years 9 months)Specialty catering. Game, central European cuisine, 1 off banquets.
I was trained in French Provincial styles and Hute cuisine. I was a Sous chef for a time with a speciality as a saucier, and brassier. I did specialty game meals for the most part.
My training was with continential kitchens and then others in the 80’s.
Languages
-
French
Limited working proficiency
-
English
Native or bilingual proficiency
Skills
Publications
-
The IT regulatory and standards compliance handbook
Syngress
This book provides comprehensive methodology, enabling the staff charged with an IT security audit to create a sound framework, allowing them to meet the challenges of compliance in a way that aligns with both business and technical needs. This «roadmap» provides a way of interpreting complex, often confusing, compliance requirements within the larger scope of an organization’s overall needs.
Key Features:
* The ulitmate guide to making an effective security policy and controls that enable monitoring and testing against them
* The most comprehensive IT compliance template available, giving detailed information on testing all your IT security, policy and governance requirements
* A guide to meeting the minimum standard, whether you are planning to meet ISO 27001, PCI-DSS, HIPPA, FISCAM, COBIT or any other IT compliance requirement
* Both technical staff responsible for securing and auditing information systems and auditors who desire to demonstrate their technical expertise will gain the knowledge, skills and abilities to apply basic risk analysis techniques and to conduct a technical audit of essential information systems from this book
* This technically based, practical guide to information systems audit and assessment will show how the process can be used to meet myriad compliance issues- Authors:
-
The Official CHFI Study Guide (Exam 312-49) For Computer Hacking Forensics Investigators
Elsevier
Audience:
Police and law enforcement personnel, military personnel, security professionals, systems administrators, legal professionals, banking, insurance, IT managers or people studying for the CHFI certification.- Authors:
-
Official (ISC)2 Guide to the CISSP(R)-ISSMP(R) CBK
ISC2
The Official (ISC)2® Guide to the ISSMP® CBK® provides an overview of management topics related to information security. This iteration provides for a more expanded enterprise model of security and management, one that delves into project management, risk management, and continuity planning. Preparing the professional for certification, as well as for job readiness, this resource promotes an understanding of what are now five ISSEP domains. These include Enterprise Security Management Practices, Enterprise-Wide System Development Security, Law, Investigations, Forensics and Ethics, Overseeing Compliance of Operations Security, and Business Continuity and Disaster Recovery Planning.
- Authors:
-
Overwriting Hard Drive Data: The Great Wiping Controversy
Information Systems Security: 4th International Conference, Iciss 2008, Hyderabad, India, December 16-20, 2008, Proceedings
Abstract. Often we hear controversial opinions in digital forensics on the re-
quired or desired number of passes to utilize for properly overwriting, some-
times referred to as wiping or erasing, a modern hard drive. The controversy has
caused much misconception, with persons commonly quoting that data can be
recovered if it has only been overwritten once or twice. Moreover, referencing
that it actually takes up to ten, and even as many as 35 (referred to as the Gut-
mann scheme because of the 1996 Secure Deletion of Data from Magnetic and
Solid-State Memory published paper by Peter Gutmann) passes to securely
overwrite the previous data. One of the chief controversies is that if a head posi-
tioning system is not exact enough, new data written to a drive may not be writ-
ten back to the precise location of the original data. We demonstrate that the
controversy surrounding this topic is unfounded.- Authors:
-
Implementing an Information Security Management System (ISMS) Training process
GIAC
- Authors:
-
Analysis of a serial based digital voice recorder
GIAC
- Authors:
-
A Taxonomy of Information Systems Audits, Assessments and Reviews
GIAC
- Authors:
-
Electronic Contracting In An Insecure World
GIAC
- Authors:
-
Requirements For Record Keeping and Document Destruction in a Digital World
GIAC
- Authors:
-
Detecting Hydan: Statistical Methods For Classifying The Use Of Hydan Based Stegonagraphy In Executable Files
GIAC
- Authors:
-
CURRENT ISSUES IN DNS
GIAC
- Authors:
-
A comparative study of attacks against Corporate IIS and Apache Web Servers
GIAC
- Authors:
-
Rationally Opting for the Insecure Alternative: Negative Externalities and the Selection of Security Controls
GIAC
- Authors:
-
A Preamble Into Aligning Systems Engineering and Information Security Risk
GIAC
- Authors:
-
There’s Nothing But Data Out There
Hakin9
In all of this, we have a society that is reliant on systems and data. Here, we see a new need to be even more vigilant than we have been in the past. When food systems are based on SCADA style controls, there is far less room for allowing rouge access to the databases and systems that run the controls that enable this future? Security has always been important, but as a future career, it is one that is not going to disappear. We may see automated systems replace even skilled jobs (such as a pilot), but it will be a long time before we start to have secure systems that do not involve people.
- Authors:
-
Secure commerce in the Mist
Hakin9
We are starting to move to IPv6 and the cloud. Right now, the uptake is minimal at best with very few early adopters for all of the hype. The climate is changing. Soon, IP addresses will be on everything and even the concept of non-disclosure agreements and contracts designed to protect intellectual property will require that we consider the nature of the cloud and the Internet as a platform for contractual negotiation.
- Authors:
-
Searching For Exploits, SCAPY Fuzzing
Hakin9
SCAPY is a series of python based scripts that are designed for network level packet manipulation. With it, we can sniff network traffic, interactively manipulate it, and fuzz services. More, SCAPY decodes the packets that it receives without interpreting them. The article is going into some of the fundamentals that you will need in order to understand the shellcode and exploit creation process, how to use Python as a launch platform for your shellcode and what the various system components are.
- Authors:
-
Extending Control, API Hooking
Hakin9
API hooking the malicious code is used to vary the library function calls and returns by replacing the valid function calls with one of the attackers choosing. The article follows from previous articles as well as goes into some of the fundamentals that you will need in order to understand the shellcode creation process, how to use Python as a launch platform for your shellcode and that the various system components are. This article includes a section on functions and calls, extending DLL injection and then move to the actual API hooking process (that we will extend) in coming articles. With these skills you will have the foundations for creating shellcode for exploits and hence an understanding of the process that penetration testers and hackers use in exploiting systems. You will see how it is possible to either create your own exploit code from scratch or even to modify existing exploit code to either add functionality or in order to bypass signature based IDS/IPS filters.
- Authors:
-
Exploiting Format Strings with Python
Hakin9
Format string attacks are not particularly new. Since
their widespread public release in 2000, format string
vulnerabilities have picked up in intensity as buffer
overflows become less common and more widely known.
From an unknown start a decade ago, they have become
a common means to exploiting system applications.
These vulnerabilities remain an issue as we still teach
them. It is not uncommon for format string vulnerabilities
to allow the attacker to view all the memory contained
within a process. This is useful as it aids in locating
desired variables or instructions within memory. With
this knowledge, an attacker can exploit the vulnerability
to successfully exploit code and even bypass control
such as Address Space Layout Randomization. In this
article Craig will discuss crafting attacks using python
in order to attack through DPA (Direct Parameter Access)
such that you can enact a 4-byte overwrite in the DTORS
and GOT (Global Access Table) and prepares the reader
for a follow-up article on exploiting the GOT and injecting
shell code.- Authors:
-
DPA Exploitation and GOTs with Python
Hakin9
This article is a follow-up and second part of a look at format strings in the C and C++ programming languages; in particular, how these may be abused. The article goes on to discuss crafting attacks using Python in order to attack through DPA (Direct Parameter Access) such that you can enact a 4-byte overwrite in the DTORS and GOT (Global Access Table).
- Authors:
-
Starting to Write Your Own Linux Schellcode
Haking
We have seen more and more people become reliant on
tools such as Metasploit in the last decade. This ability to
use these tools has empowered many and has created a
rise in the number of people who can research software
vulnerabilities. It has created more security professionals
who cannot only scan a target for vulnerabilities using
a tool such as Nessus, but who can complete tests
involving system exploitations and hence validate the
results presented to them by a scanner. But, this ends
when a new application with unexpected calls or controls
is found. What do we do when presented with a special
case? This makes it extremely difficult for signature
based systems to stop or detect shellcode created for
a specific purpose and hence more likely that the tester
will succeed in testing the vulnerability without other
controls interfering. If we remain at this level, we will
stop the lower level attacker, but fail in stopping more
sophisticated attacks. You will learn how to write your
own shellcode, how to fix all the nulls and how to validate
your shellcode.- Authors:
-
Beyond Automated Tools and Frameworks: the shellcode injection process
Hakin9
Automated frameworks (including Metasploit) have simplified the testing and exploitation process. This of course comes with a price. Many penetration testers
have become tool jockeys with little understanding of
just how software functions. This script kiddie approach
to code testing does have its place. It has allowed us to
drastically increase the number of people working on
testing systems for vulnerabilities and in assessing the
risks these pose. At the same time, if these individuals
do not progress further, simply relying on the ability to
leverage the efforts of others, we will hit bottlenecks in
the creation of new tests and processes. This article is
going to follow from previous articles as well as going
into some of the fundamentals that you will need in order
to understand the shellcode creation process, how to use
Python as a launch platform for your shellcode and that
the various system components are.- Authors:
-
Understanding conditionals in shellcode
Hakin9
This article is going to follow from previous articles as well
as going into some of the fundamentals that you will need
in order to understand the shellcode creation process. In
this article, we are looking at extending our knowledge
of assembly and shellcoding. This is a precursor to the
actual injection and hooking process to follow. You will
investigate how you can determine code loops, the uses
of loops as well as acting as an introduction into how
you can reverse engineer assembly or shellcode into a
higher level language and even pseudo-code, all of which
forms an essential component of creating and executing
one’s own exploit successfully. By gaining a deep
understanding just how code works and to know where to
find the fundamentals shellcode programming language
we hope to take the reader from a novice to being able to
create and deploy their own shellcode and exploits.- Authors:
-
Taking control, Functions to DLL injection
Hakin9
DLL injection is one of the most common methods
used by malware such as a rootkit to load it into the
host’s privileged processes. Once injected, code can
be inserted into functions being transmitted between
the compromised code and a library function. This
step is frequently followed with API hooking where
the malicious code is used to vary the library function calls and returns. This article is part of a monthly series
designed to take the reader from a novice to being able
to create and deploy their own shellcode and exploits.
With this knowledge, you will learn just how easy it is for
sophisticated attackers to create code that can bypass
many security tools. More, armed with this knowledge
you will have the ability to reverse engineer attack code
and even malware allowing you to determine what the
attacker was intending to launch against your system.- Authors:
-
THE ECONOMICS OF DEVELOPING SECURITY EMBEDDED SOFTWARE
SECAU
Abstract Market models for software vulnerabilities have been disparaged in the past citing how these do little to lower the risk of insecure software. In this paper we argue that the market models proposed are flawed and not the concept of a market itself. A well-defined software risk derivative market would improve the information exchange for both the software user and vendor removing the often touted imperfect information state that is said to believe the software industry. In this way, users could have a rational means of accurately judging software risks and costs and as such the vendor could optimally apply their time between delivering features and averting risk in a manner demanded by the end user. It is of little value to increase the cost per unit of software by more than an equal compensating control in an attempt to create secure software. This paper argues that if the cost of an alternative control that can be added to a system is lower than the cost improving the security of the software itself, then it is uneconomical to spend more time and hence money improving the security of the software. It is argued that a software derivative market will provide the mechanism needed to determine these costs.
Keywords – Security, Derivatives, vulnerability market, software development, game theory- Authors:
-
- Craig Steven Wright,
- Tanveer A Zia
-
A quantitative analysis into the economics of correcting software bugs
CISIS’11 Proceedings of the 4th international conference on Computational intelligence in security for information systems
Using a quantitative study of in-house coding practices, we demonstrate the notion that programming needs to move from «Lines of Code per day» as a productivity measure to a measure that takes debugging and documentation into account. This could be something such as «Lines of clean, simple, correct, well-documented code per day», but with bugs propagating into the 6th iteration of patches, a new paradigm needs to be developed. Finding flaws in software, whether these have a security related cost or not, is an essential component of software development. When these bugs result in security vulnerabilities, the importance of testing becomes even more critical. Many studies have been conducted using the practices of large software vendors as a basis, but few studies have looked at in-house development practices. This paper uses an empirical study of in-house software coding practices in Australian companies to both demonstrate that there is an economic limit to how far testing should proceed as well as noting the deficiencies in the existing approaches.
- Authors:
-
- Craig Steven Wright,
- Tanveer A. Zia
Certifications
-
GIAC Security Expert (GSE)
GIAC, License 16
– -
GIAC Security Expert Malware (GSE-Malware)
GIAC, License 22
– -
GIAC Security Expert Compliance (GSE-Compliance)
GIAC, License 1
– -
GIAC Security Essentials GSEC (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 10056
– -
GIAC Certified Firewall Analyst GCFW (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 1891
– -
GIAC Certified Windows Security Administrator GCWN
GIAC, License 1234
– -
GIAC Certified ISO-27000 Specialist G2700 (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 39
– Present -
GIAC Certified Intrusion Analyst GCIA
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 2913
– Present -
GIAC Certified Windows Security Administrator GCWN
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 1234
– Present -
SANS Cyber Guardian Program (https://www.sans.org/cyber-guardian/listings.php)
SANS Cyber Guardian Program https://www.sans.org/cyber-guardian/, License Red/Blue
– Present -
GIAC Information Security Fundamentals GISF
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 1444
– Present -
GIAC Certified Incident Handler GCIH (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 5896
– Present -
GIAC Certified UNIX Security Administrator GCUX
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 587
– Present -
GIAC Certified Forensic Analyst GCFA (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 265
– Present -
GIAC Systems and Network Auditor GSNA (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 571
– Present -
GIAC Security Leadership GSLC (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 2178
– Present -
GIAC Reverse Engineering Malware GREM (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 586
– Present -
CISSP Certified Information Security Professional
ISC2, License 47304
– Present -
CISSP-ISSMP Information Systems Security Management Professional
ISC2, License 47304
– Present -
CISSP ISSAP Information Systems Security Architecture Professional
ISC2, License 47304
– Present -
CISA Certified Information Systems Auditor
ISACA
-
CISM Certified Information Security Manager
ISACA
-
GIAC Assessing and Auditing Wireless Networks GAWN
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 894
– Present -
GIAC Information Security Professional GISP
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 1978
– Present -
GIAC Legal Issues in Information Technology & Security GLEG (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 6
– Present -
GIAC Certified Project Manager GCPM (GOLD)
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 128
– Present -
GIAC Penetration Tester GPEN
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 7262
– Present -
GIAC Secure Software Programmer- .NET GSSP-.NET
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 263
– Present -
GIAC Web Application Penetration Tester GWAPT
GIAC http://www.giac.org/certified-professional/craig-wright/107335, License 2358
– Present -
GSAE
GIAC, License 141
– Present -
GNET
GIAC, License 129
– Present -
GIAC Law of Fraud
GIAC
-
GIAC Reverse Engineering Malware
GIAC
-
GIAC Intrusion Prevention
GIAC
-
SANS Stay Sharp Master Packet Analysis
GIAC
-
Stay Sharp: Defeating Rogue Access Points
GIAC
-
GIAC Web Application Security
GIAC
-
Stay Sharp – Google Hacking and Defense
GIAC
-
GIAC Security Policy and Awareness
GIAC
-
GPCI GIAC Payment Card Industry
GIAC
-
GIAC Leadership Management
GIAC
-
CCE Certified Computer Examiner
ISFCE http://www.isfce.com/ccelist.htm, License 480
Education
-
University of London
Master of Science (MSc), Finance (Quantitative Finance)
–Econometrics
-
SANS Institute
Master of Science (M.Sc.), Information Security Management
– -
SANS Technology Institute
Master of Science Degree in Information Security Engineering (MSISE), Information Systems – Security
–The Master of Science Degree in Information Security Engineering Curriculum:
http://www.sans.edu/academics/curricula/msise
All of the papers and primary work is complete.
http://www.giac.org/certified-professional/craig-wright/107335
-
Charles Sturt University
PhD, Computer Science
–Incorporates:
• Economic theory,
• Quantitative financial modelling,
• Algorithmic game theory and
• Statistical hazard/survival models.
The models will account for Heteroscadastic confounding variables and include appropriate transforms such that variance heterogeneity is assured in non-normal distributions. Process modelling for integrated Poisson continuous-time process for risk through hazard will be developed using a combination of:
• Business financial data (company accountancy and other records),
• Legal databases for tortuous and regulatory costs and
• Insurance datasets.
This data will be coupled with hazard models created using Honeynets (e.g. Project Honeynet), reporting sites such as the storm centre. The combination of this information will provide the framework for the first truly quantitative security risk framework.Activities and Societies: The Quantification of Information Systems Risk The goal of this research project is to create a series of quantitatively models for information security. Mathematical modelling techniques that can be used to model and predict information security risk will be developed using a combination of techniques.
-
Charles Sturt University
MSD, Masters in Systems Development
–See
http://www.itmasters.edu.au/WhichQualification/MasterofSystemsDevelopment/MicrosoftMCSDNet35Stream.aspxActivities and Societies: Java, C#, C, C++
-
Charles Sturt University
Psychology, Psychology
–Activities and Societies: Associate Student at present. Have completed. Foundations of Psychology
-
University of Newcastle
Master of Statistics (MSTAT), Quantitative Statistics
–Longitudinal Data Analysis
Statistical Inference
Data Mining
Business Research Methods
Regression and Forecasting
Decision Analysis
Statistical Computing
Heteroscedastic Modelling
Financial time series
Bayesian Analysis
Generalised Linear ModelsActivities and Societies: This programme involves undertaking skills training programmes, and learning through originality in solving problems offering the ability to plan and implement tasks at a professional level. Topics include: regression and ANOVA, mathematical statistics, research methods, statistical inference, generalised linear models, time series and stochastic processes, statistical computing, total quality management, Bayesian methods, data mining, surveys and experiments, multivariate statistics.
-
Northumbria University
LLM, Law (International Commercial Law)
–LLM (eCommerce Law)International Commercial Law
* Competition Law
* International Trade Finance Law
* International Finance Law
* Banking Law
* Law of International Trade
* Competition Law
* Contract Law (advanced)
* Tort and Negligence OnlineActivities and Societies: LLM (eCommerce Law)International Commercial Law
-
Charles Sturt University
Master of Information Systems Security (MInfoSysSec), IT Security
–Design Secure Distributed Networks
IT Risk Management
Network Security Fundamentals
Theory of Computation
IT Management Issues
Network and Security Admin
Information Security
Principles of Database Development
Object Modelling
SysDev Project ManagementActivities and Societies: Advanced skills in the design, implementation and management of secure networks Higher order network design An informed and reflexive perspective on IT Security issues Problem-solving and troubleshooting and documenting complex problems The ability to analyse complex client business security requirements and select appropriate solutions Skills in the development of leading edge security solutions that meets customer business objectives for functionality and performance
-
Sans Institute
GSE-Compliance, GSE-Malware, GIAC Security Expert (Compliance Stream)
– -
Charles Sturt University
Master of Management (MMgt), Management, Finance
–HRM571 Managing People in the Information Age
ITC563 IT Management Issues
MKT571 Marketing for IT Managers
FIN571 Managerial Finance
MGT572 Managing Organisational Change
MGT573 Strategic PracticeActivities and Societies: The aim of this course is to prepare students to succeed in management positions that leverage computing technology to operate and expand business endeavours. The needs of existing IT managers, programmers, developers, network engineers, and other IT workers who aspire to move upward into technical management positions will be catered to with the emphasis on exploiting information technologies for productivity and competitiveness.
-
Charles Sturt University
Master of Network and Systems Administration (MNSA), IT Networking
–Subject: ITC-511 Networking Concepts 1
Subject: ITC-512 Networking Concepts 2
Subject: ITC-513 Wireless Networking Concepts
Subject: ITC-514 Network and Security Administration
Subject: ITC-593 Network security
Subject: ITC-506 Topics in IT Ethics
Subject: ITI-555: Operating System Essentials
Subject: ITI-556: Supporting a Network Infrastructure (I)
Subject: ITI-557: Supporting a Network Infrastructure (II)
Subject: ITI-558: Active Directory Infrastructure
Subject: ITI-559: Designing Active directories and Network InfrastructureActivities and Societies: Advanced design, implementation and network management skills Higher order system administration skills Advanced skills in identifying network security risk profiles, defining security policies and maintaining secure global networks Problem-solving methodologies to troubleshoot and document global internetworking problems Analyse complex client business and technical requirements Development of solutions that meets customer business objectives for functionality, performance, and cost
-
Guess (I am an ex-chatholic who is now involved in the UC)
Doctor of Theology, Comparitive Religous and Classical Studies
–Ask me and I may share. I act as a lay pastor and I do not always desire to argue with people who have no concept of religion. I was a catholic, became an atheist, and moved towards the uniting church as I learnt more in science and mathematics.
If you need to ever need to know of Dionysus, Vesta, Menrva, Ceres (Roman Goddess of the Corn, Earth, Harvest) or other Mythological characters – I am your man. I could even hold a conversation on Eileithyia, the Greek Goddess of Childbirth and her roman rebirth as Lucina.
I bet you did not know that Asklepios Aesculapius is the Greek God of Health and Medicine or that Lucifer is the name of the Roman Light-bearer, the God and Star that brings in the day.
Activities and Societies: A comparitive study of Greko-Roman foundations to the Judeo-Christian origins of the Eve belief and myth structure. If you are really lucky (or unlucky as the case my be) I may let you read my dissertation: «Gnarled roots of a creation theory».
-
Fuel Sciences
Associate of Science (Organic Chemistry)
– -
Nuclear Physics
Nuclear Physics, Nuclear magnetic resonance (NMR)
– -
University of Queensland
Engineering, Computer Systems Engineering (incomplete – changed to Comp Sci in 4th year – I was young)
– -
Padua College
HIgh School, Senior Certificate
– -
IT – Summary of qualifications and achievements
A summary of some (some mind you) of my Certifications, Information Technology (Security)
GSE-Compliance # 0001 [Platinum] GIAC Security Compliance
GSEC # 10506
G7799 # 0039
GCFA # 0265
GSNA # 0571
GSAE # 0141
GLEG # 0006
GLFR # 0016 GIAC Law of Fraud (GLFR)
GREM # 0586 GIAC Reverse Engineering Malware (GREM)
GPCI # 0086 GIAC Payment Card Industry (GPCI)
GSPA # 0101 GIAC Security Policy and Awareness (GSPA)
GLDR # 0101 GIAC Leadership (GLDR)
GWAS # 0535 GIAC Web Application Security (GWAS)
GIPS # 0036 GIAC Intrusion Prevention (GIPS)
GCUX # 0587 GIAC Certified UNIX Security AdministratorMCSA # 3062393 Microsoft Certified Systems Administrator
MCSE # 3062393 Microsoft Certified Systems Engineer
MCSE # 3062393 Microsoft Certified Systems Engineer (Mail)
MCSE # 3062393 Microsoft Certified Systems Engineer (Security)
MCDBA # 3062393 Microsoft Certified Database AdministratorMIEEE # 87028913 Member IEEE
AFAIM # PM133844 Associate Fellow Aust Inst. Management
MACS # 3015822 Senior Member Aust Computer SocietyActivities and Societies: CISSP # 47302 (ICS)2 Security Professional ISSMP # 47302 (ICS)2 Security – Management Professional ISSAP # 47302 (ICS)2 Security – Architecture Professional CISA # 0542911 Certified Information Systems Auditor CISM # 0300803 Certified Information Security Manager CCE # 480 ISFCE – Certified Computer Examiner ISSPCS # 051 International Systems Security Professional Certification Scheme
Interests
- Music (Piano) Research Learning
Patents
-
Application number: 20140359291
United States 20140359291
Issued- Inventors:
Recommendations
A preview of what LinkedIn members have to say about Craig Steven:
-
Craig is a little bit crazy, as in Orville & Wilbur Wright craziness of deciding to add an engine to a glider. … a true visionary.
-
Craig has a vast array of knowledge and experience at his disposal. He keeps his commitments and gets along with with other team members. He does quality work.
Groups
-
Aurora Cybercrime & Cyberconflict Research Group
-
ASX Network
-
Venture Capital – Public Equity – Funding – Investment
-
Global OWASP Foundation
-
Information Security Community
-
Information Systems Security Association (ISSA) Discussion Forum
-
Information Security

Craig Steven Wright





Dejar un comentario
¿Quieres unirte a la conversación?Siéntete libre de contribuir!